Premium Photo | Female hand with mobile phone withdrawing money from atm using nfc contactless wifi pay pass system wireless authentication and data transmission security in finance and banking

Symmetry | Free Full-Text | Research on a Vehicle Authentication and Key Transmission Protocol Based on CPN

H1EAX series" High-capacity and highly accurate module | Finger Vein Authentication Modules for Embedding in Devices | Products and Solutions | Hitachi Industry & Control Solutions, Ltd.

Energies | Free Full-Text | Biometric Authentication-Based Intrusion Detection Using Artificial Intelligence Internet of Things in Smart City

Processes for authentication and confidentiality of mobile voice and... | Download Scientific Diagram

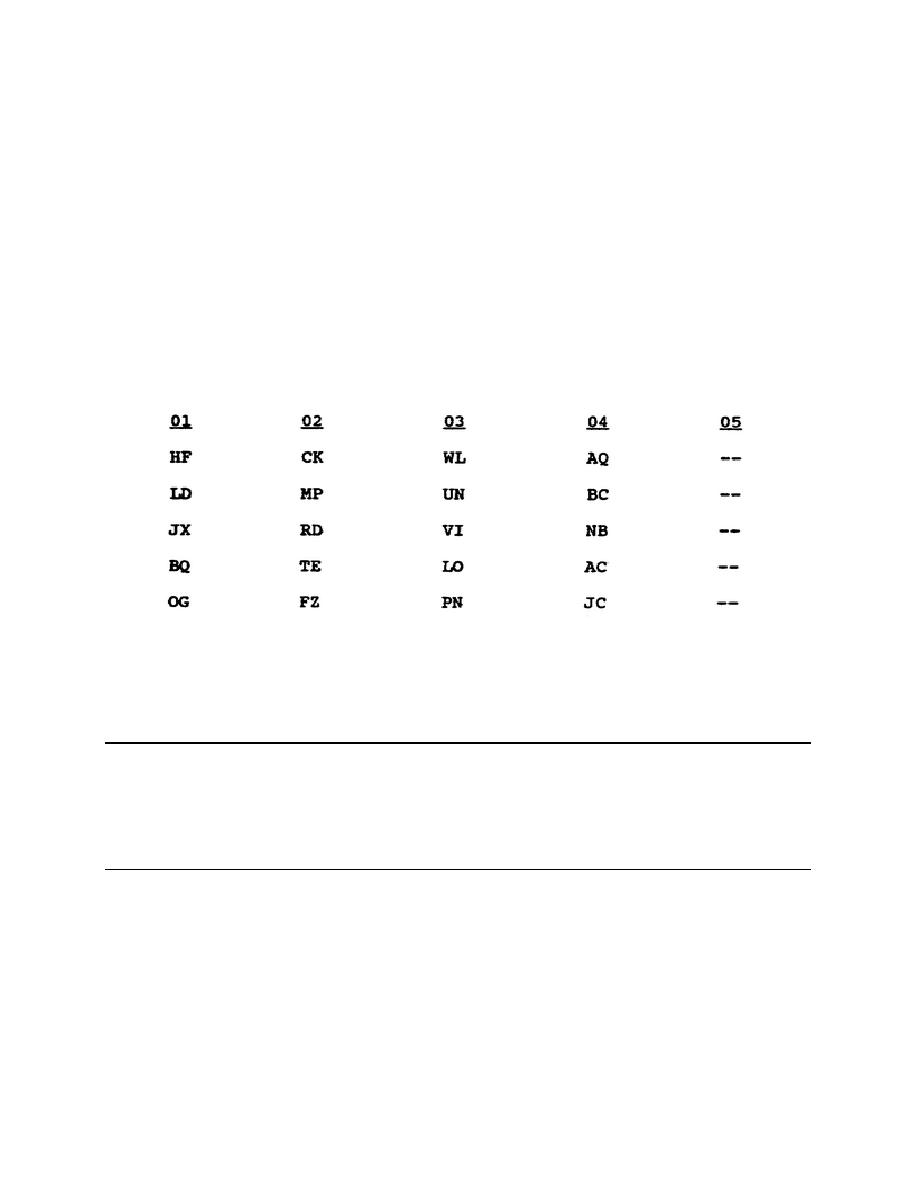
PCI Requirement 8.2.1 – Use Strong Cryptography to Render All Authentication Credentials Unreadable During Transmission and Storage

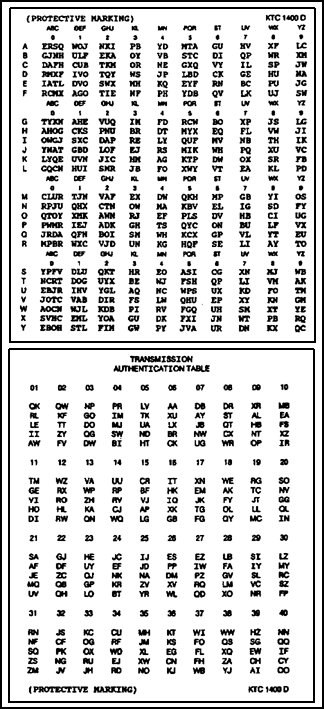
What is navigation message authentication? - Inside GNSS - Global Navigation Satellite Systems Engineering, Policy, and Design
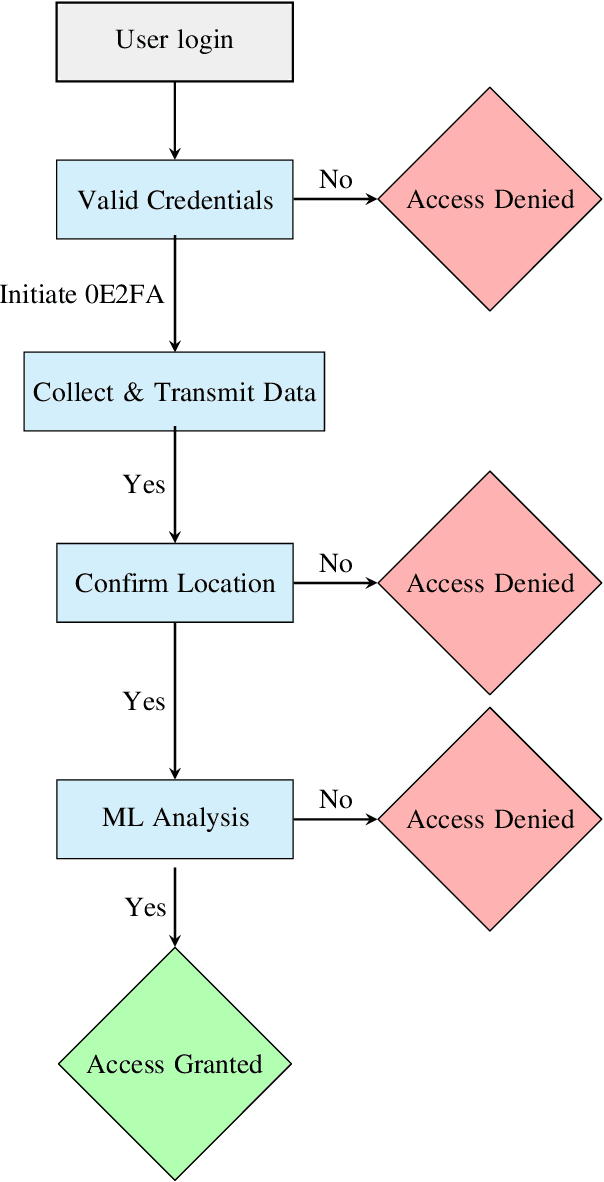
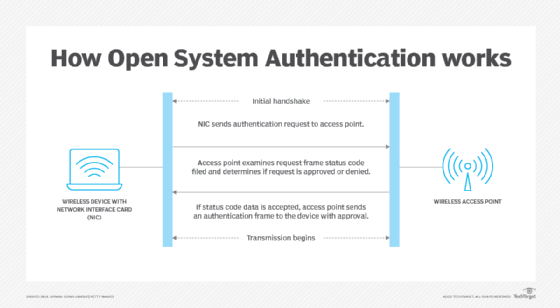
Zero-Effort Two-Factor Authentication Using Wi-Fi Radio Wave Transmission and Machine Learning: Paper and Code - CatalyzeX

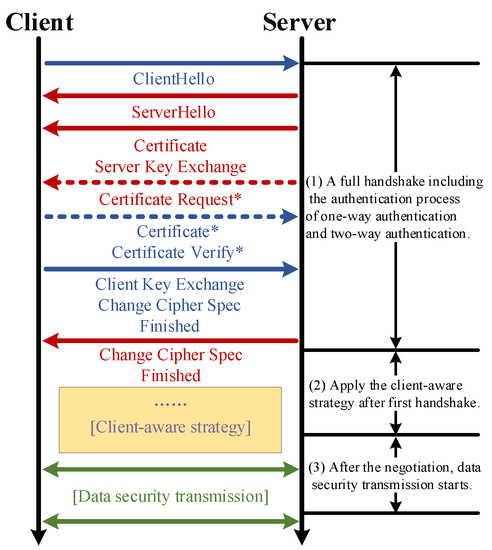
A flow diagram of client-aware secure data transmission methods. The... | Download Scientific Diagram

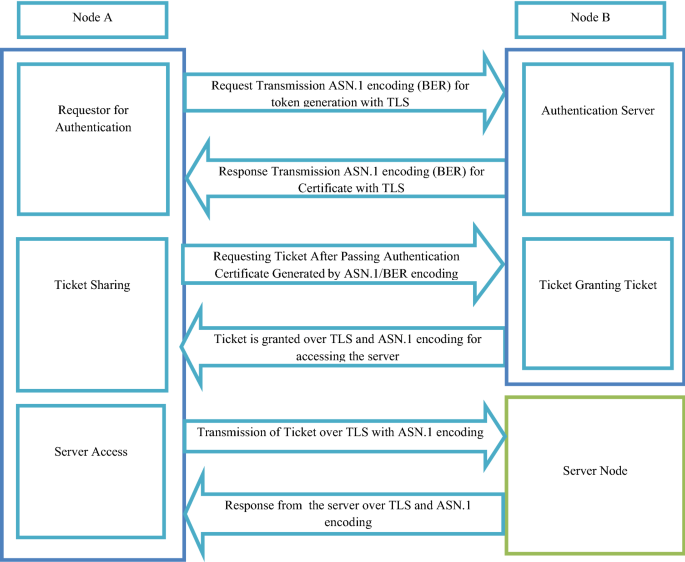
Securing Data Transmission and Authentication. Securing Traffic with IPSec IPSec allows us to protect our network from within IPSec secures the IP protocol. - ppt download

Encryption, authentication, and transmission - Amazon Web Services (AWS) Video Tutorial | LinkedIn Learning, formerly Lynda.com